Why website security matters - a practical example.
This happens all too often, someone will contact me and try to sell me something, an IT service, a new way of doing things, it doesn't matter.
The thing is, if I'm contacted out of the blue like this I consider it permission to check out the company that you represent. This goes doubly so if you're a security company. So, what do I do?
Well, let's take a real world example here. Viadex.com contacted me several times on linkedin so I went to the website to have a look at who they are, what they offer and, how the website is built.
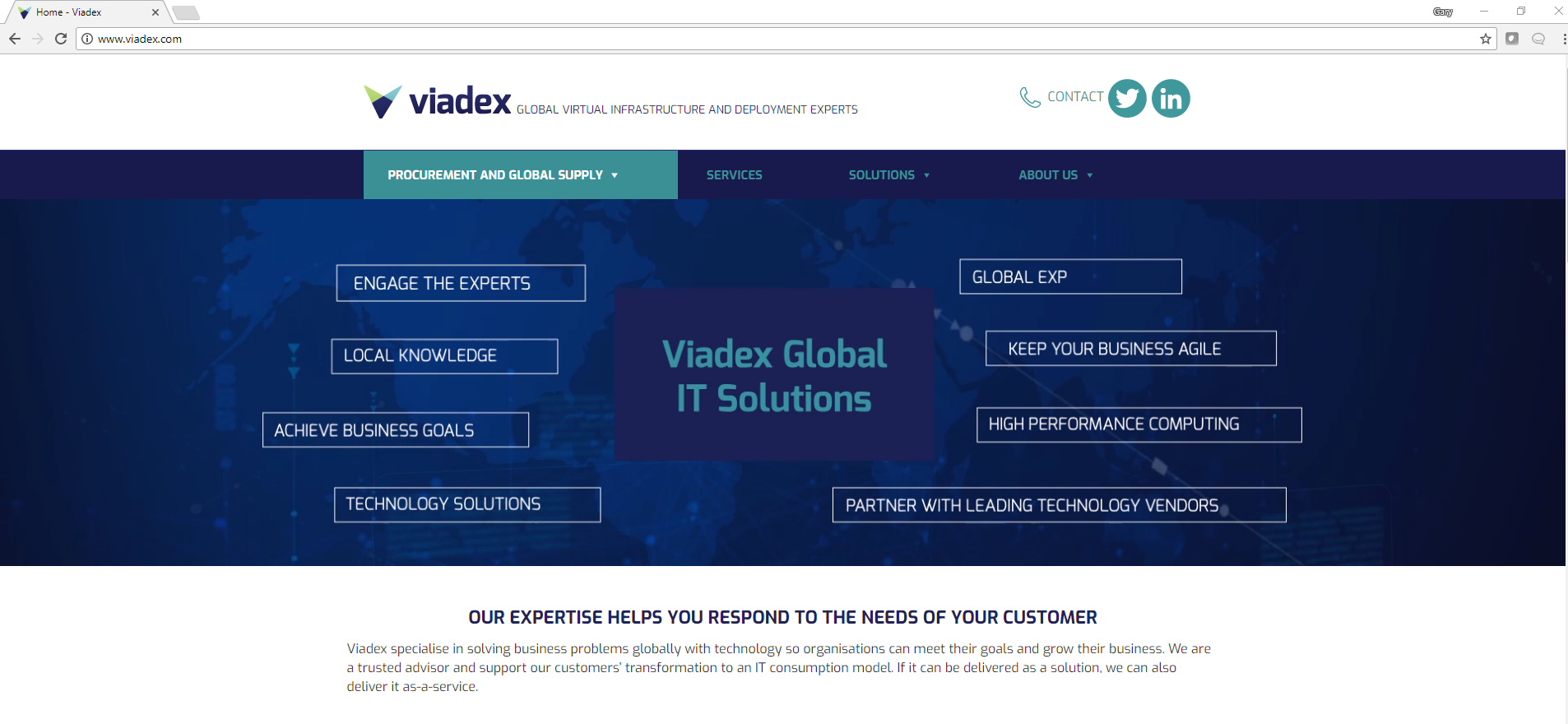
The site itself looks quite nice:
The first problem I see though is that the site doesn't use HTTPS. Today there is NO EXCUSE for not using HTTPS. The moment I see no HTTPS it's already looking bad for you.
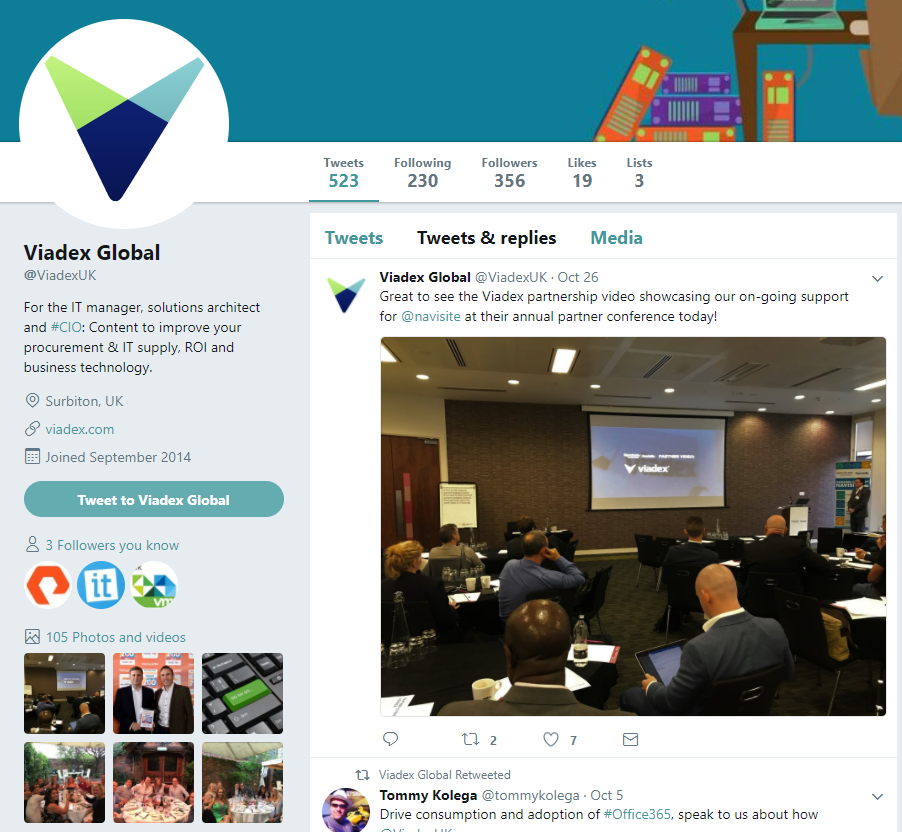
The next thing I do is have a look at twitter. In this case Viadex have 356 followers and they, never, ever, ever reply to tweets and nor can I DM (direct message) them. That tells me straight away that the account is a bot. No one replies from it and no one monitors it. Ignoring social media is another black mark:
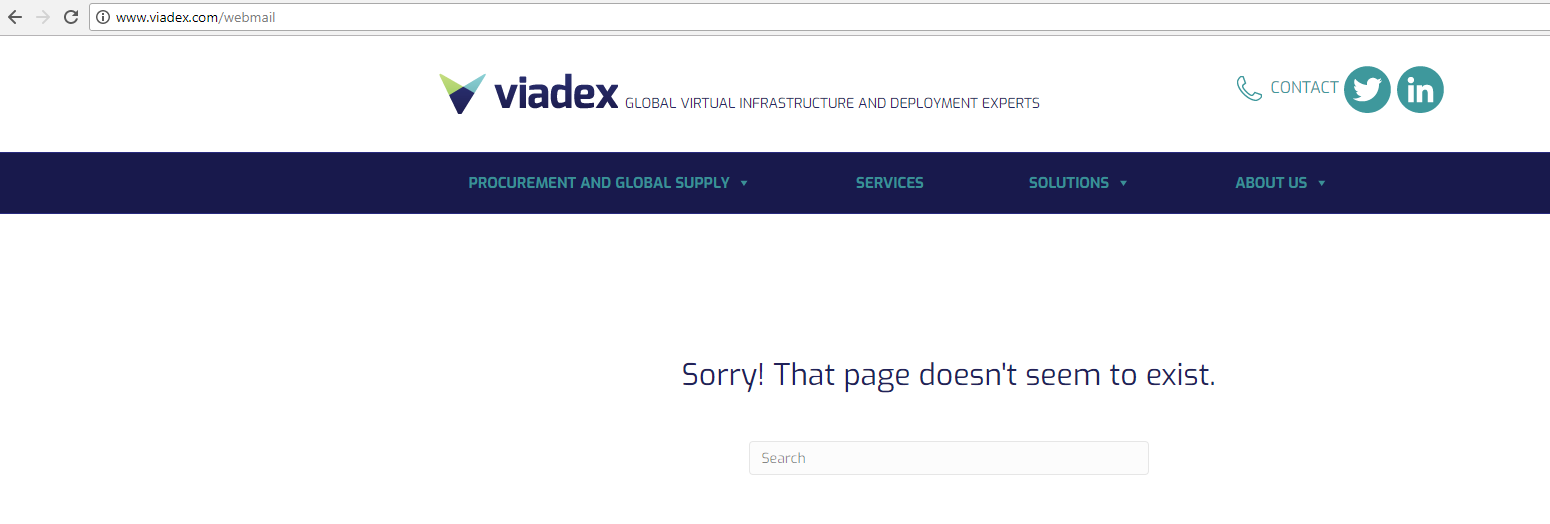
At this point I suspect that I'm dealing with a company that really doesn't quite get me as an IT person so I start to dig a little deeper. Almost every company has a webmail URL attached to their website. The first thing I tried was viadex.com/webmail and that gave me:
No joy and a decent 404 as it doesn't tell me anything about the site. This is good, Ok, lets try webmail.viadex.com:
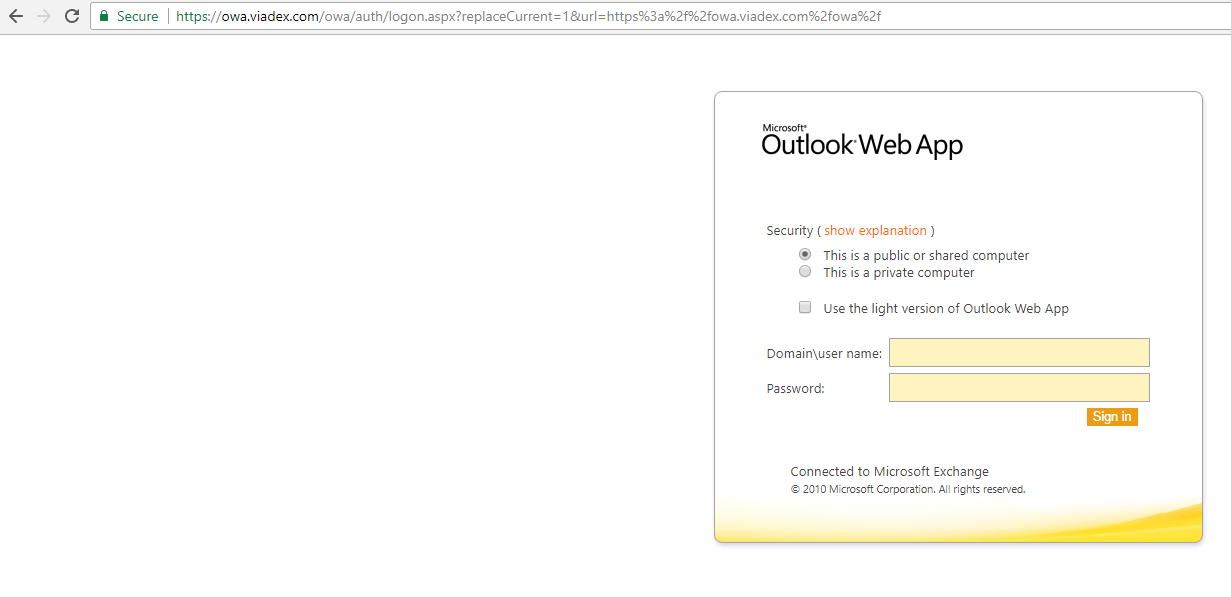
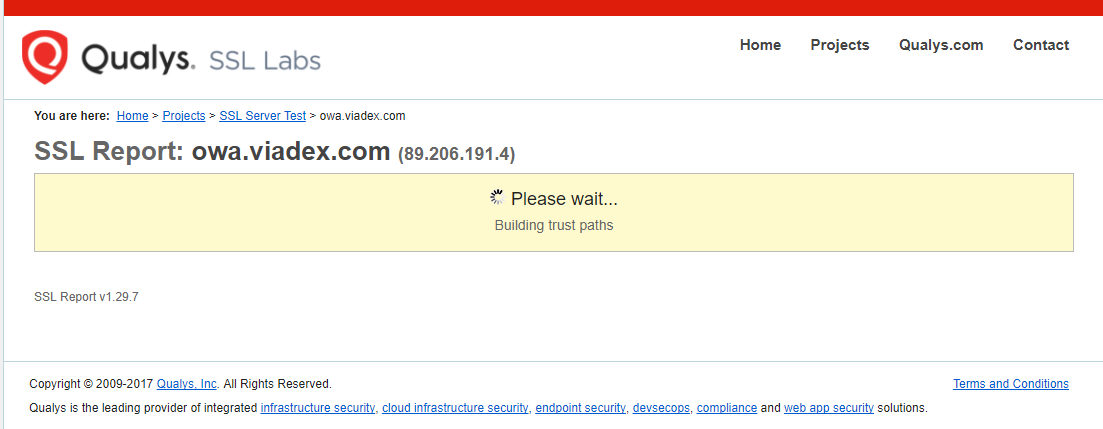
Bingo! Ouch though! 7 year old OWA means a 7 year old exchange server. Maybe patched. Maybe not. Exchange 2010 doesn't come out of extended support until January 2020 so it could still be patched but I have a feeling it's not. They do use HTTPS though which is a good sign. Of course, me being me I do this:
Yup, I get Qualys to have a look at the cert because that'll tell me if you know the basics of HTTPS, in this case, they don't:
It's taken me about 20 minutes to write this and collect the screenshots. The actual testing took about 5 minutes. I'm not a security person but even I can tell that this company doesn't understand security. At this point I messaged them on twitter and over email to their "info@viadex.com" email address only to get a bounceback from a users account that says "Hi, I've left the company now". This adds further fuel to the fire that they basically don't know what they are doing.
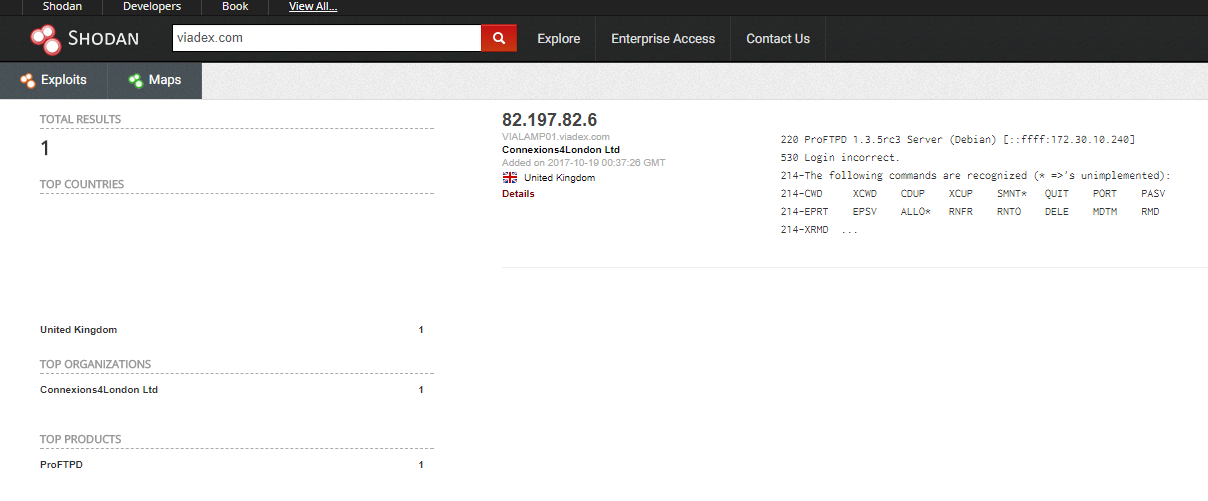
Once I've attempted to contact them I keep digging, this is getting interesting now. The next thing I do is go to Shodan and look up "viadex.com":
Interesting. The site runs proftpd 1.3.5rc3 - Let's see what the CVE database shows shall we? Heading over www.cvedetails.com and doing a search for "proftpd" shows me a nice remote access vulnerability (http://www.cvedetails.com/cve/CVE-2015-3306/). This even has a link to a python script that will use the vulnerability. Again, I'm NOT an infosec person, this stuff is FREELY available to anyone who has a few minutes to look into it all.
Back to shodan which shows me that SSH is open - this is always a mistake, the script kiddies will hit SSH with hundreds of logon attempts a day. It also shows me that the viadex.com server is on 82.197.82.6
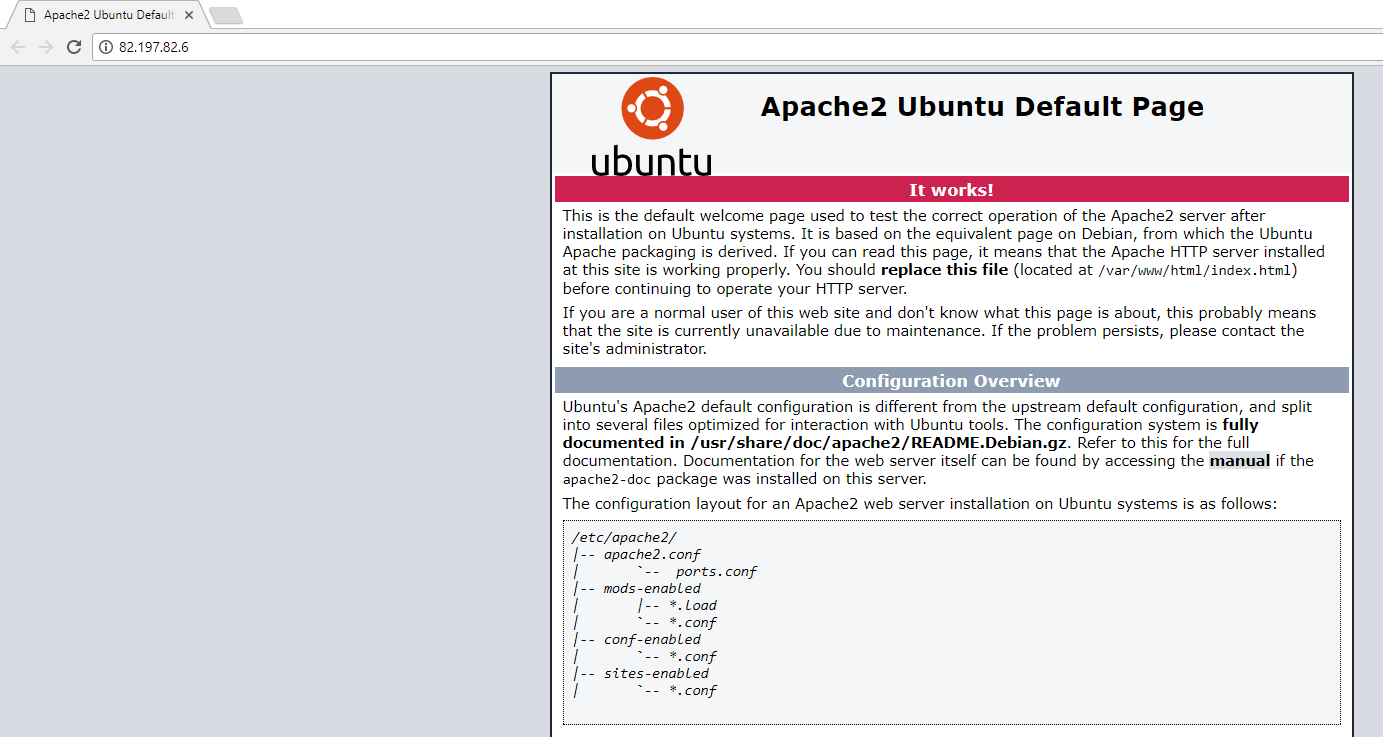
Connecting to the IP and:
Yup. An Apache 2 Ubuntu default page. This is just how professional this IT services company are.
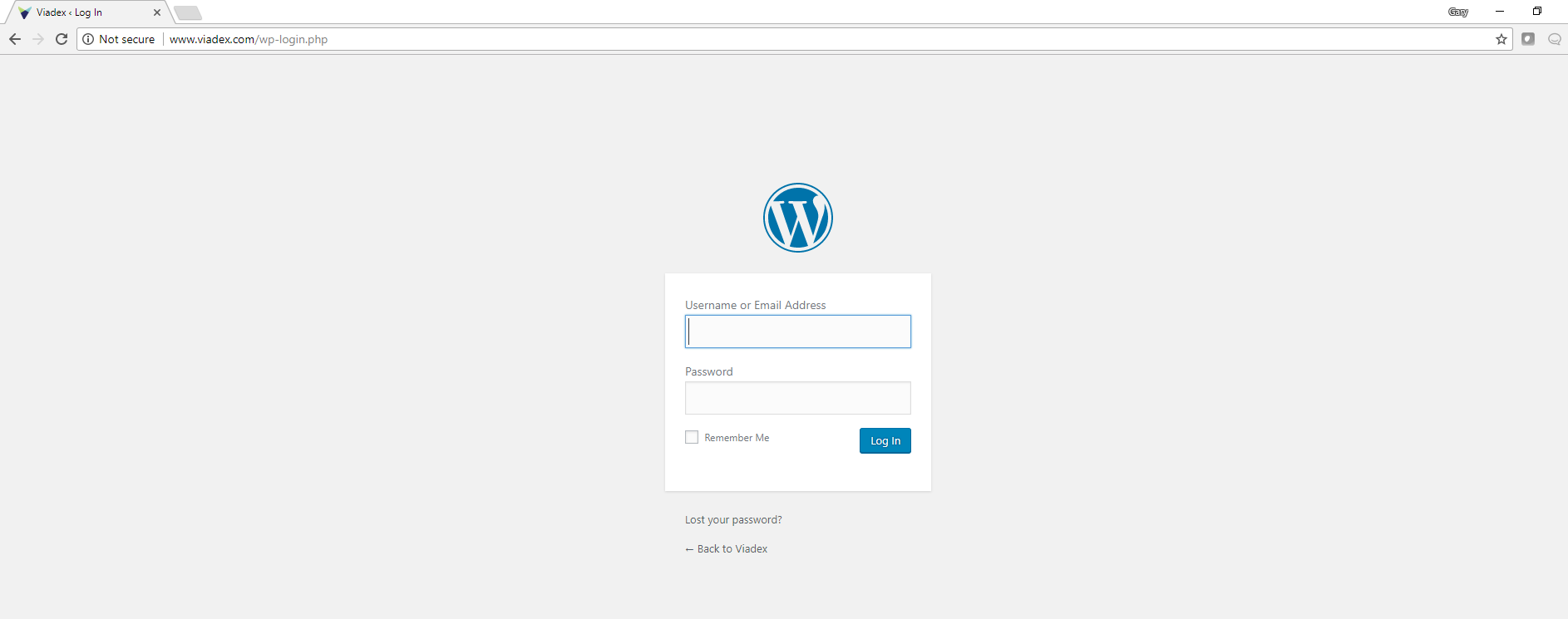
Of course, there is even more. The site is based on wordpress which I picked up by a quick glance at the debugging tools in Chrome. If you've not looked at Chromes additional tools please do, they are utterly amazing. Anyway, wordpress has a default admin page under /wp-login so............
Yup, the admin page for wordpress exposed to the world and not encrypted.
I'm not trying to show off how "good" I am at this stuff because I'm not. What I'm showing is that even an amateur like me can find out with just 15 minutes of digging around the code of a site and trying a few default URL's. A malicious actor would most likely already be in the site and exfiltrating the data.
We all have to be better than this, we all need to open up and listen when someone says "I think I've found a vulnerability on your website", we have to be more responsible about what we expose on the internet and how that data is handled. GDPR is around the corner, this stuff MATTERS and I will call you to account for it not because I'm being difficult but because I care about IT security and I call about what data could be lost because of a careless error.
EDIT: I have heard back from them and they have a "plan to fix things" and I've been asked to retest at a later date.
Subscribe to Ramblings of a Sysadmin
Get the latest posts delivered right to your inbox