Deploying a root CA via a GPO
Following on from my post about using an internal CA for internal sites, I thought it worth a quick blog entry to show how to deploy a custom CA to your windows based clients via a GPO.
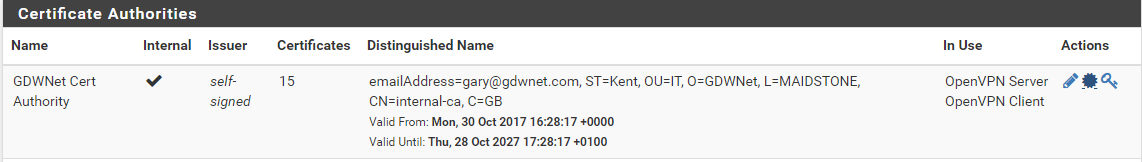
PFsense, my internal CA has a special certificate which is the root CA. All certs are generated from this cert and, as such, they trust the root cert. As long as my clients trust the CA cert they'll trust any certs it generates.
From PFSense, I can export the root CA certificate, just like any other cert it's just a CRT file:
Once I have that file, I jump onto a domain controller, launch the GPMC (Group Policy Management Console) and create a GPO that deploys this cert to the trusted cert store on my windows servers and desktops.
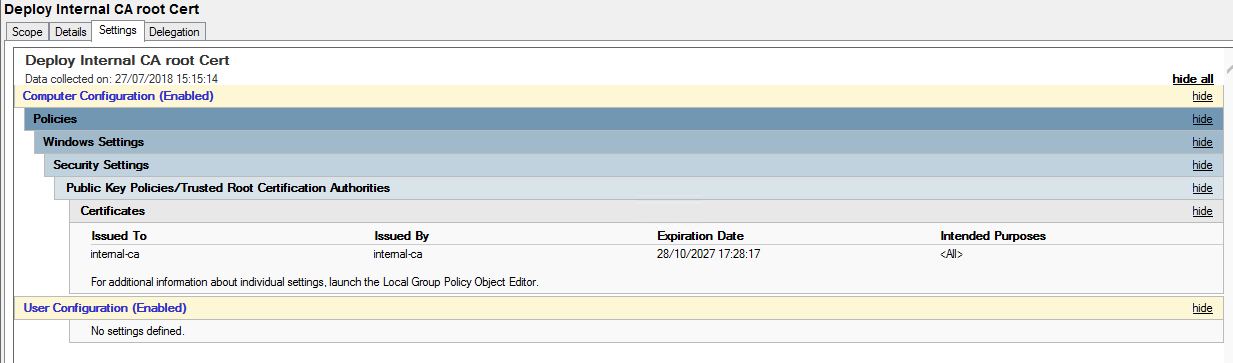
The policy is a computer policy and can be found under:
Computer configuration -> Policies -> Windows Settings -> Security Settins -> Public Key -> Trusted Root certification authorities -> Browse for the CRT file and then save the policy and link it to the domain:
I could put this cert into the Default Domain Policy but I like to have one GPO for one task as it makes admin easier later on, if I need to change the cert I know exactly which policy it is and exactly what that policy does.
Once the GPO is created, a gpupdate /force or just wait and done!
Subscribe to Ramblings of a Sysadmin
Get the latest posts delivered right to your inbox